On the recent VMProtect leaks and why it is a bad thing
You may have seen the recent word about the VMProtect source being leaked to various openly accessible places like GitHub. For obvious reasons I won’t link it here, but from the brief looks that I got, it indeed looks sophisticated enough that it could be the real deal. People embraced this news as a great thing, an early 2023 Christmas gift to the reversing community:
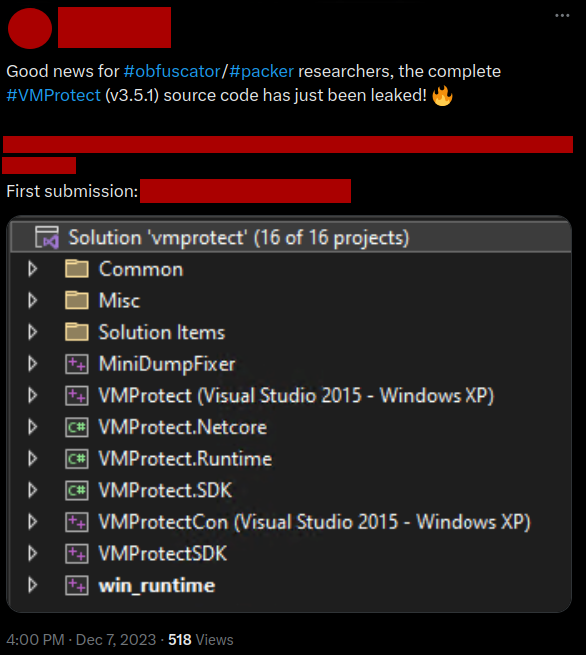 A tweet promoting the leak of the source code of VMProtect. Authors have been blurred.
A tweet promoting the leak of the source code of VMProtect. Authors have been blurred.
News spread very quickly. By the time of writing this post, one of the GitHub repositories that hosts the leaked code now has over 1K stars and forks. And that does not include all the other non-fork copies of the repository and ZIP archives that people probably have uploaded everywhere:
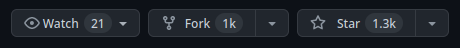 GitHub stars of one of the repositories containing the leaked code.
GitHub stars of one of the repositories containing the leaked code.
Is this release really a good thing though?
Disclaimer
This is an opinionated post. Chances are you will not agree with me. And that’s fine. I am open to having a discussion about it in the comments or in private, as long as it is civil.
Let me also preface this with the following:
- I am not affiliated with VMPSoft.
- I do not use their products. Most of my projects are open-source and thus do not need obfuscation.
- I do not own a license nor am paid by VMPSoft to say this and/or defend them.
- I do not wish to start a witch hunt to any of the people involved. It is counter-productive.
- This post is not just about VMProtect, but about code / intellectual property leaks in general, and how we as a community should deal with them in my opinion.
The good news
Having access to such a complete repository comes with some really nice benefits:
- Open source is great for research, especially for new, aspiring reverse engineers and obfuscator developers.
- Everyone in the RE community can see how the professionals create obfuscators, and learn from it greatly.
- It will be easier to create analysis tools and deobfuscators, which can be used to help analyzing malware that (ab)use the obfuscator.
- We can even help VMPsoft making their product better! More eyes on the same code means more bugs can be spotted and/or fixed.
- Free stuff always tastes sweet!
In general, I agree with this sentiment. I am a huge proponent of open-source software. Most of my projects are open-source. The projects that I use or base my research on are often also open-source code, and I strongly believe that things being open-source results in better products in the long term.
The bad news
However, in this particular case, what this appraisal will also do is the following:
- People will copy this, claim it as their own, modify it, repackage and resell it, all without the explicit consent of VMPsoft, the company behind VMProtect.
- There will be more threat actors abusing VMProtect for bad purposes (e.g., using it to hide malicious intent), as there is now free, uncontrolled access to a ready-to-use tool without a third party that can retract licenses in case of misconduct.
- It can incur serious damage to VMPsoft in sales and reputation-wise, even if no full deobfuscator is built.
- It will also set the standard that publishing things that should not be published results in lots of approval and sensationalism. This gives an incentive to bad guys to keep doing bad things, something I think we all should try to avoid.
- A general distrust will emerge in the reverse engineering community where people will get even more secretive about their research than what we already are. I have already seen this in some of the sub-communities that exist. People are very cautious with who they share what with. To be in a research community where nobody trusts each other is really bad, and I would hate to see this distrust grow even further.
The general response
If we look at the general response to the leak, we see posts like the following:
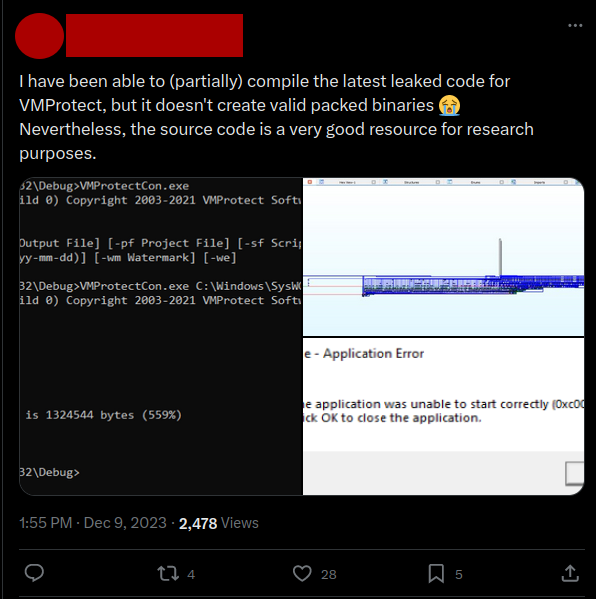 Positive responses to the leak. Tweet authors have been blurred.
Positive responses to the leak. Tweet authors have been blurred.
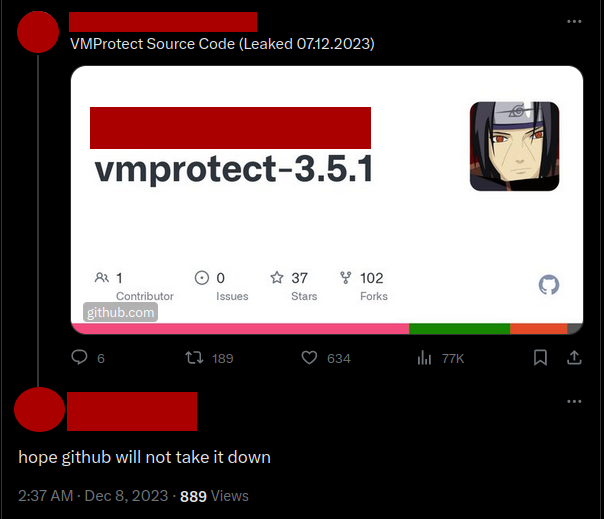 Positive responses to the leak. Tweet authors have been blurred.
Positive responses to the leak. Tweet authors have been blurred.
 Positive responses to the leak. Tweet authors have been blurred.
Positive responses to the leak. Tweet authors have been blurred.
I hope this is just the news bubble that I am in and that I am wrong, but it seems (almost) nobody seems to care. On the contrary, it seems that we as a community are actually wholeheartedly accepting this type of behavior, which blows my mind.
“But wait, open-source software also gets abused!”
You could argue, these things could happen with any open-source product. Other open-source obfuscators have unfortunately undergone a very similar fate. For example, many malware developers have used the ConfuserEx project to protect their latest payload and make it harder to analyze it. Various so-called “Red-team Tooling” also have been used and abused in the past to achieve similar goals.
The problem, however, is control and consent. No matter how you look at it, this is a classic case of intellectual property theft.
- VMPSoft is a small company.
- They build a product that they put 10+ years of research and development time into it.
- They chose to sell it as a service. The code behind their product was not meant to be shared.
- Leaking and using this code is therefore stealing intellectual property.
- Stealing is bad and unethical.
Besides, reverse engineering a protected binary can be done without the full source code of the obfuscator. It has been done many times in the past and will happen in the future. There was no legitimate need for this whatsoever.
“But wait, this is better than letting people sell it on the black market!”
Some people have also expressed that in the event of such a leak, publishing and sharing it fully open source is still the best thing one could do. The main arguments behind this point are the following:
- We should not incentivize people to sell leaks to the highest bidder and instead let everyone benefit equally.
- Bad actors can bug leaked binaries with malware and distribute them to people who are searching for a “cheaper solution”. If everything is public and open, this is significantly more difficult to do.
However, these are in my opinion flawed arguments.
Consider a scenario where a database full of usernames, credentials and/or secrets is dumped. Does that mean that in such a case we should just publish it for everyone to use? Sure enough, the leaker cannot benefit anymore from reselling it, nor can it be bugged with malware. However, we are still leaking private data for everyone to use and abuse, and, more importantly, let it all happen in an uncontrolled manner.
I don’t think people realize how much harm this does to VMPSoft itself, software developers using VMP, legitimate users of VMP, as well as the reverse engineering and security community in general.
So what should we do as a community?
I think we should stop praising this and start openly condemning this type of behavior, or at least make people aware of the consequences that these types of leaks have. We do this not by starting a witch hunt on the people who report on news or repost links (I think for a lot of people it really is a case of ignorance), but by educating people and reporting repositories for leaked content, intellectual property theft or other types of fraud/misconduct. A good education on the topic is far more valuable than just calling people out.
Please don’t publish and/or use stolen content. It is not your right nor should it be.